1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
| read(0, "11111111111111111111111111\n", 1024) = 27
syscall_0x14f(0x1, 0, 0x3131313131313131, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x3131313131313131, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0x1, 0x3131313131313131, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x4, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x51e7647e, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x2, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0xe0b4140a, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0xe6978f27, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x152(0x1, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x1, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0x1, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x6, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x4, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x53a35337, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x5, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x2, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x9840294d, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x5eae4751, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x1, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x152(0, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x153(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x3131313131313131, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x3131, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0x1, 0x3131, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x4, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x51e7647e, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x2, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0xe0b4140a, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0xe6978f27, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x152(0x1, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x1, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0x1, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x6, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x4, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x53a35337, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x5, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x2, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x9840294d, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x5eae4751, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x1, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x152(0, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x153(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0x1, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x4, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x51e7647e, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x2, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0xe0b4140a, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0x1, 0xe6978f27, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x152(0x1, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x1, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0x1, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x2, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x6, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x4, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x53a35337, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x2, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x5, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x2, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x9840294d, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0, 0x3, 0x1, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x14f(0x1, 0, 0x5eae4751, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x1, 0x3, 0, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0x3, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x152(0, 0x2, 0x3, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x150(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x151(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x153(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
syscall_0x154(0, 0, 0x2, 0xffffffffffffff80, 0, 0x55c3d6f28890) = -1 ENOSYS (Function not implemented)
newfstatat(1, "", {st_mode=S_IFCHR|0620, st_rdev=makedev(0x88, 0xb), ...}, AT_EMPTY_PATH) = 0
unlink("/tmp/my_module") = -1 ENOENT (No such file or directory)
delete_module("my_module", O_NONBLOCK) = -1 ENOENT (No such file or directory)
write(1, "Congratulations!", 16) = 16
lseek(0, -1, SEEK_CUR) = -1 ESPIPE (Illegal seek)
exit_group(0) = ?
+++ exited with 0 +++
|
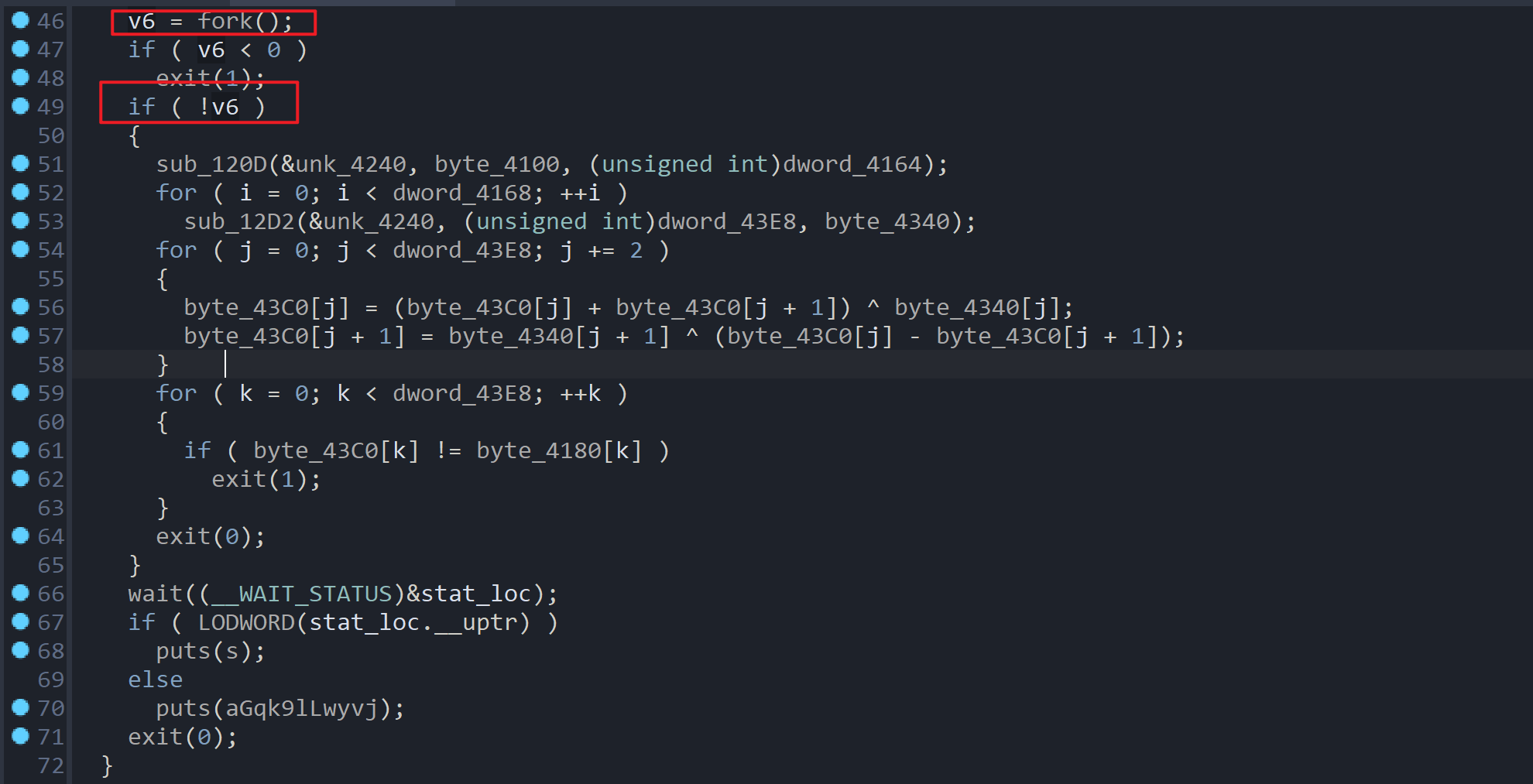
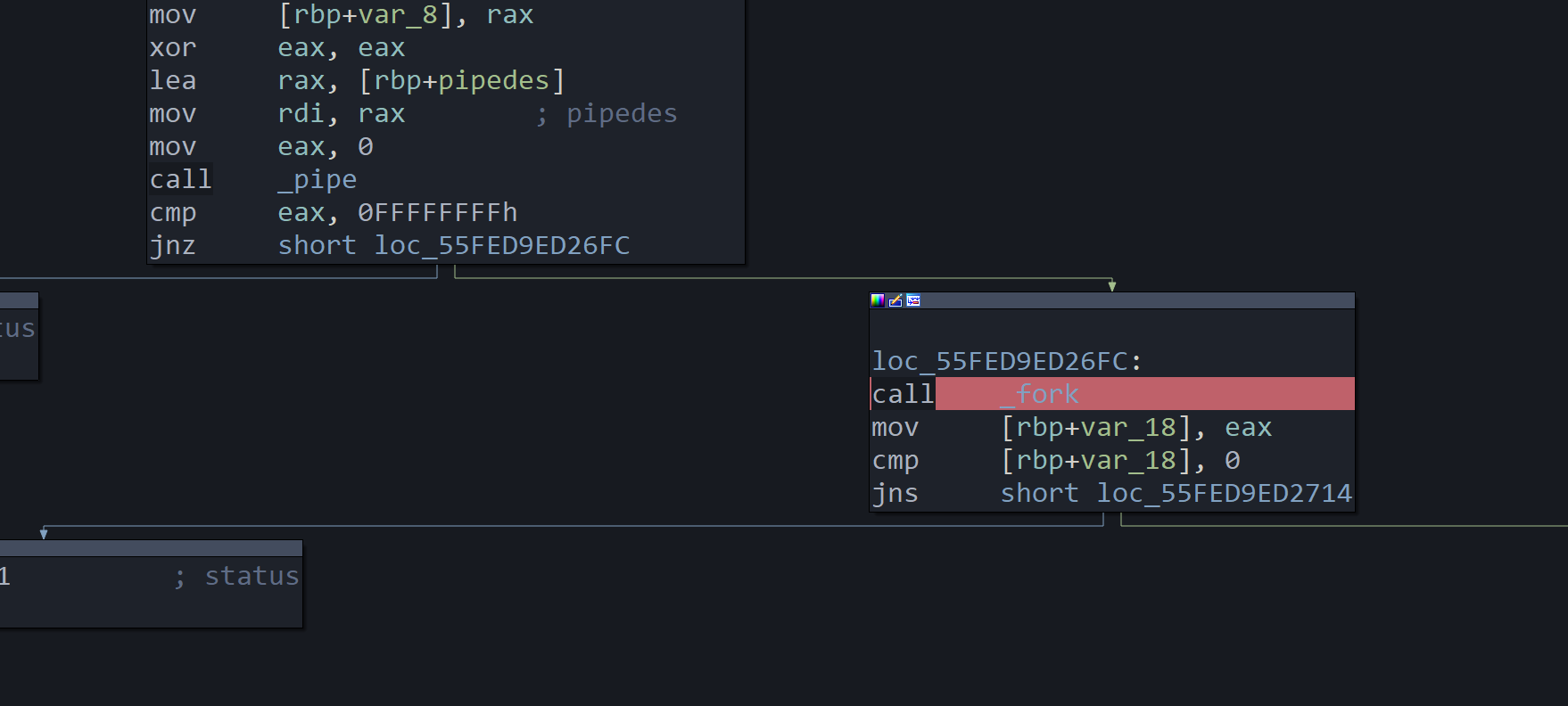
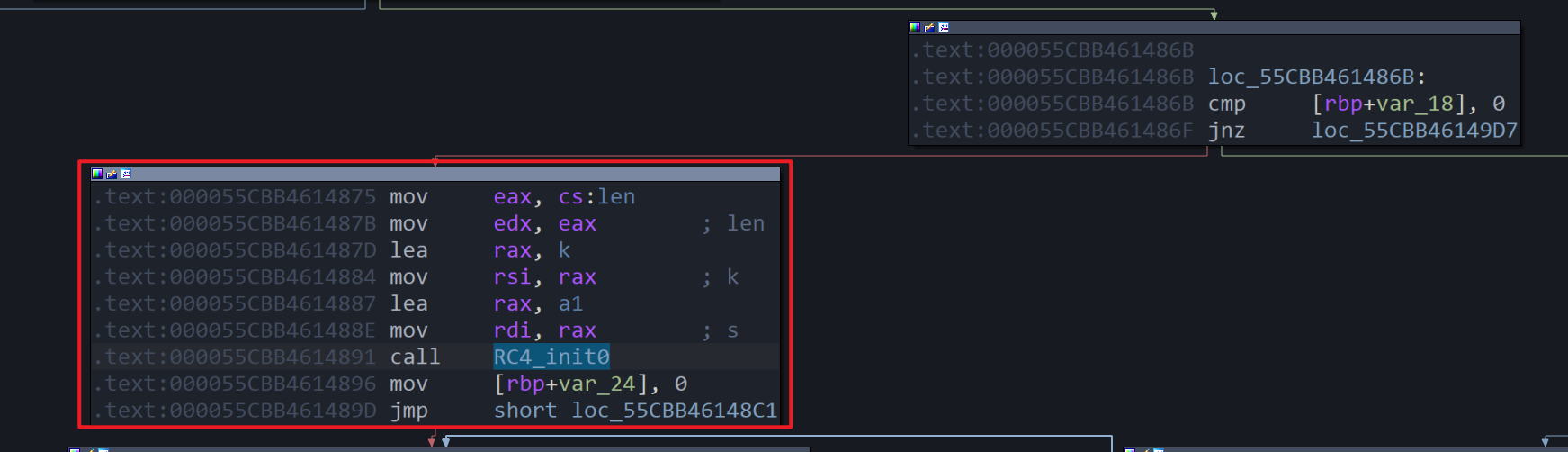 将
将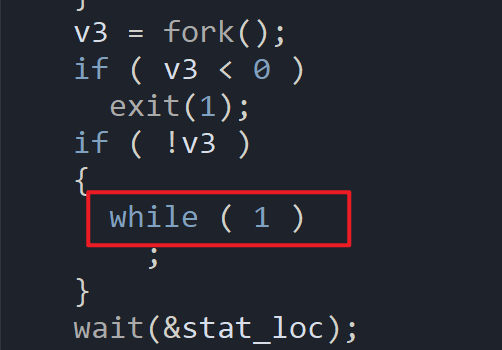 \
\
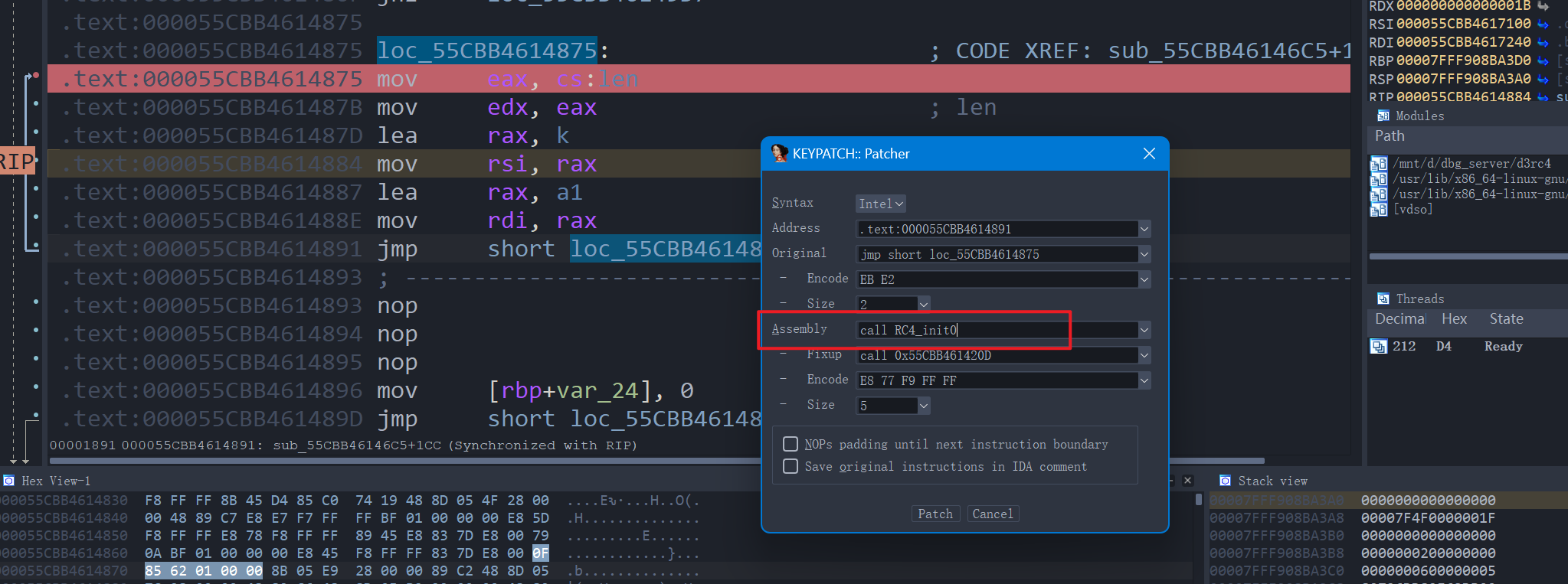
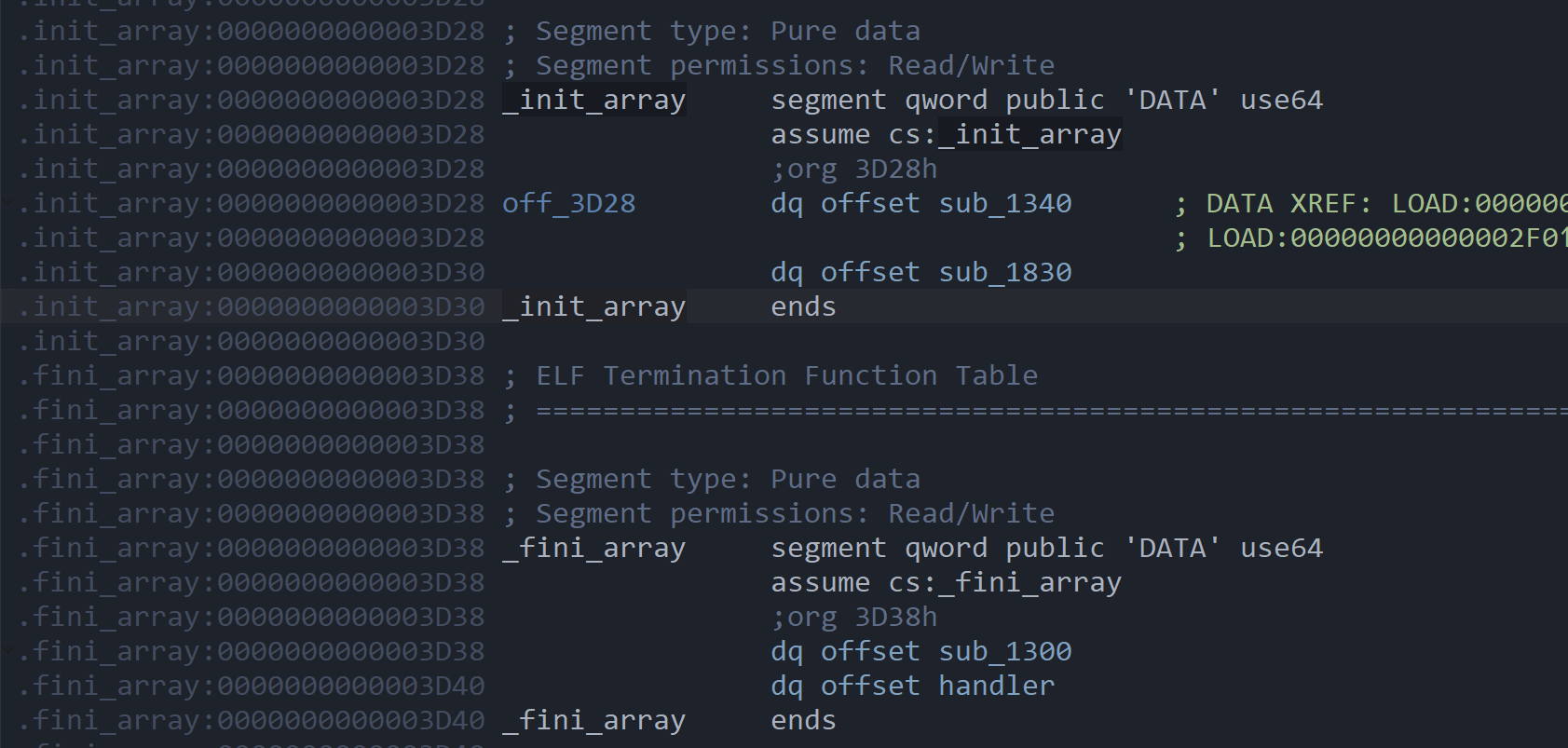 断在
断在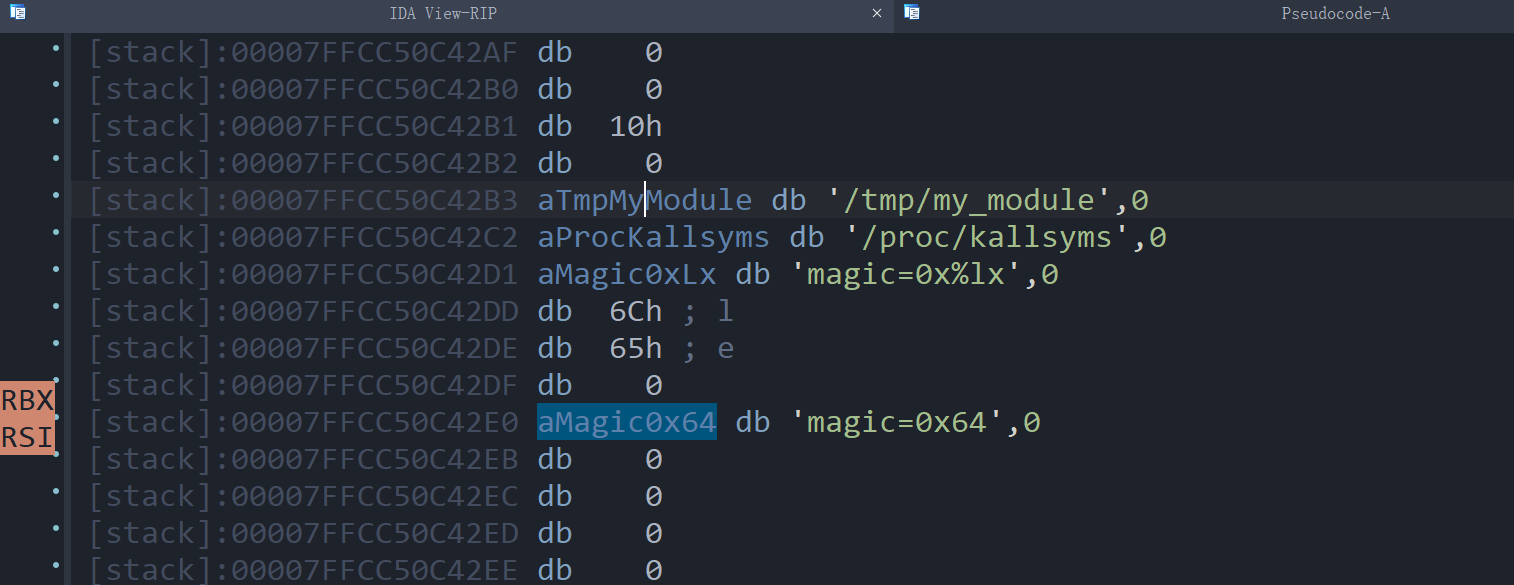
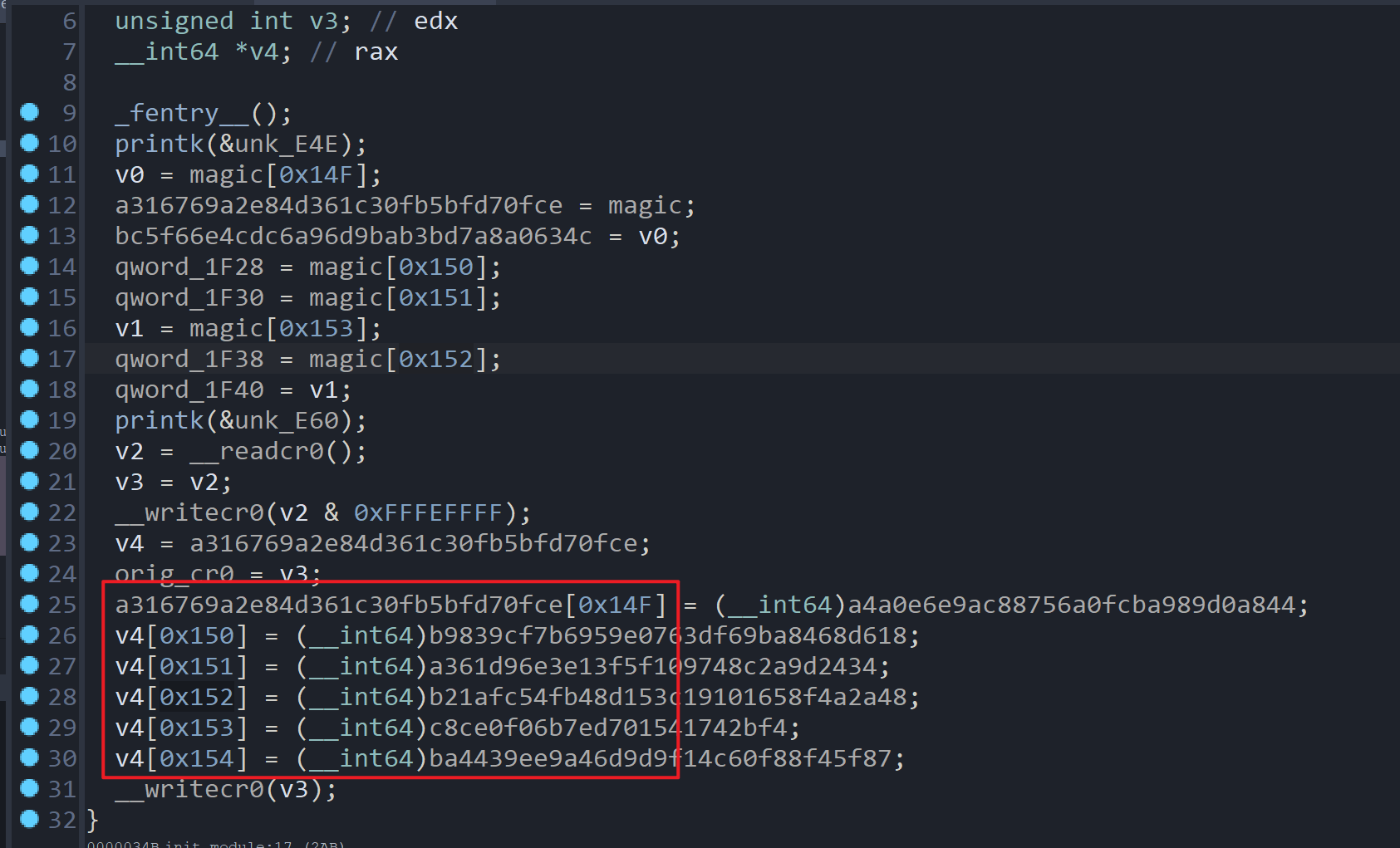
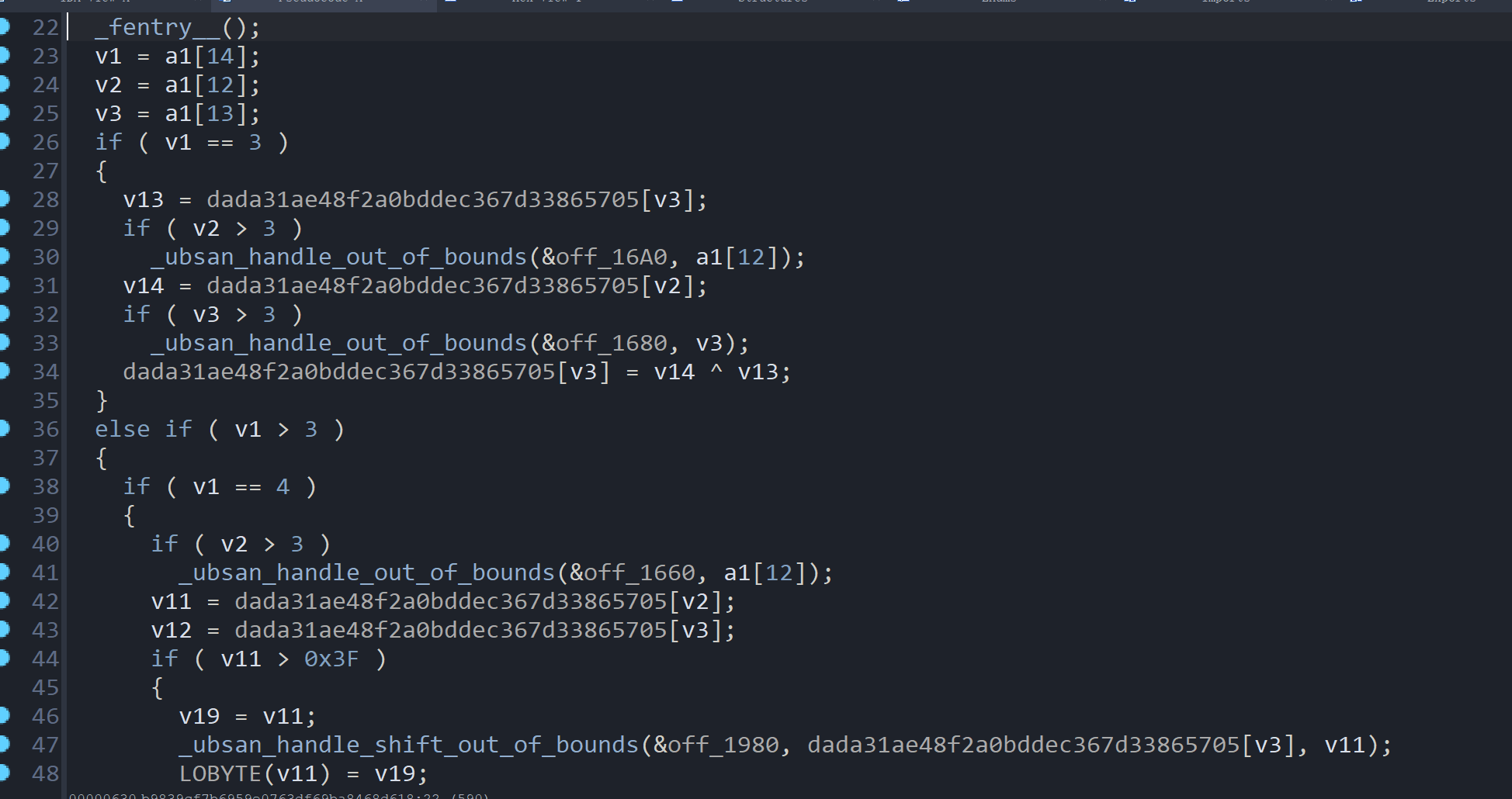
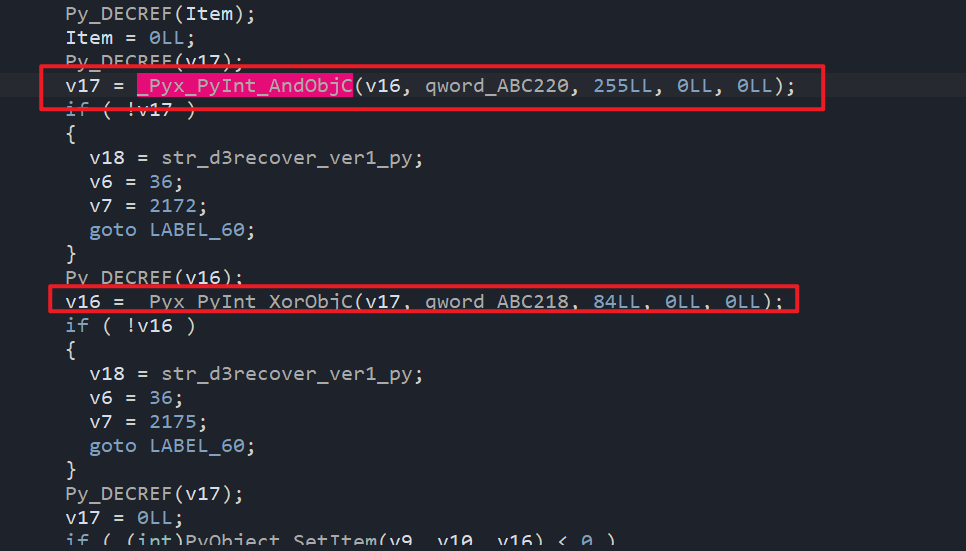
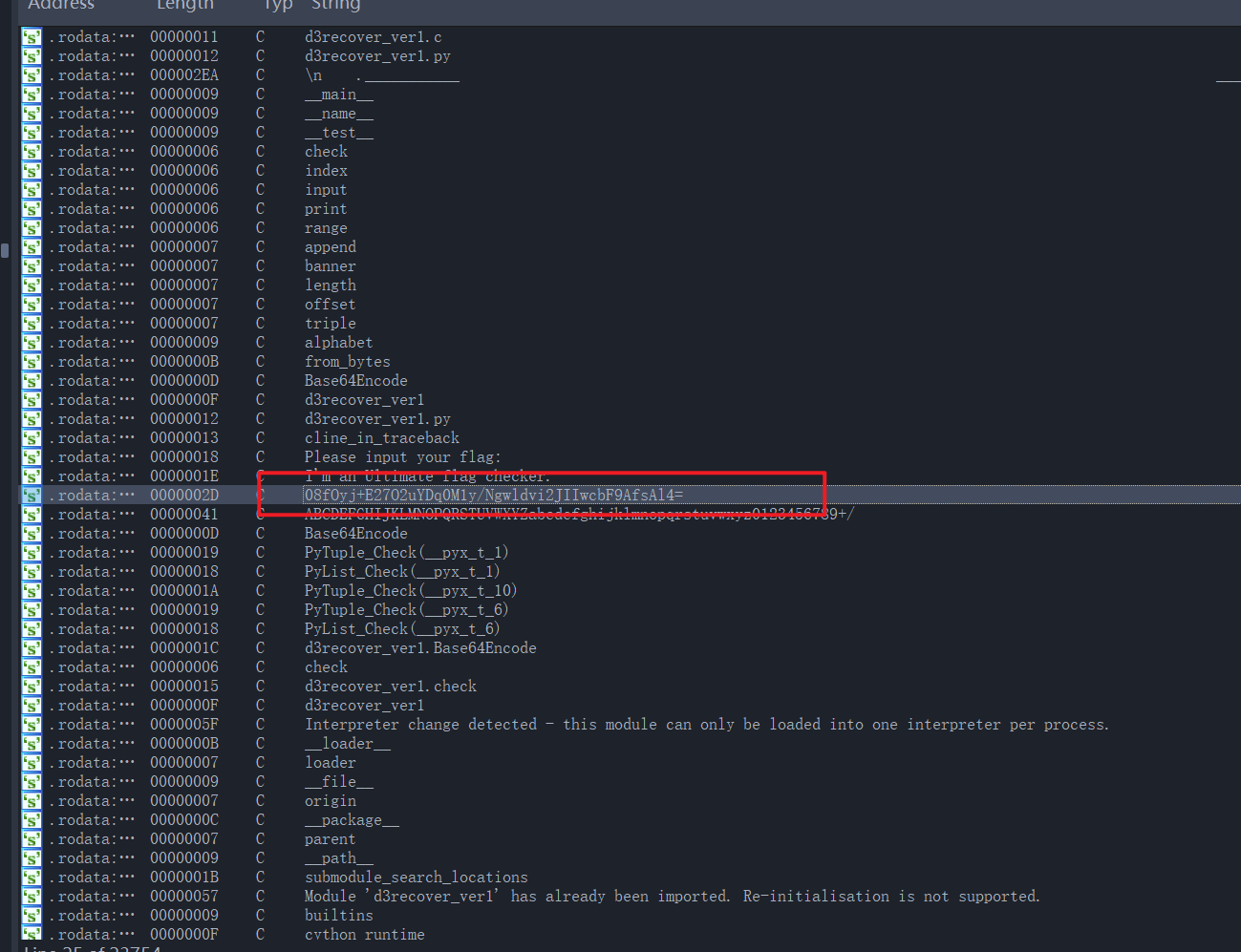 转化后为
转化后为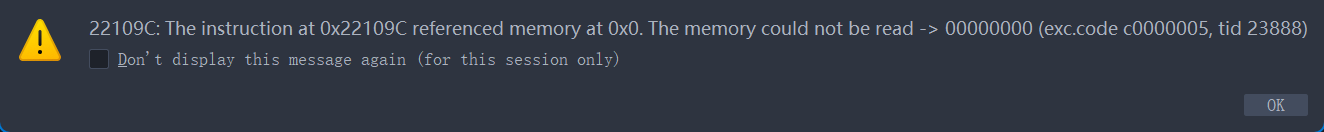 可以通过
可以通过