2023年春秋杯冬季赛 RE Writeup
本文最后更新于 2024年1月27日 凌晨
2023年春秋杯冬季赛 Reverse 题解
UPX2023
0x0 脱壳
工具一键脱壳
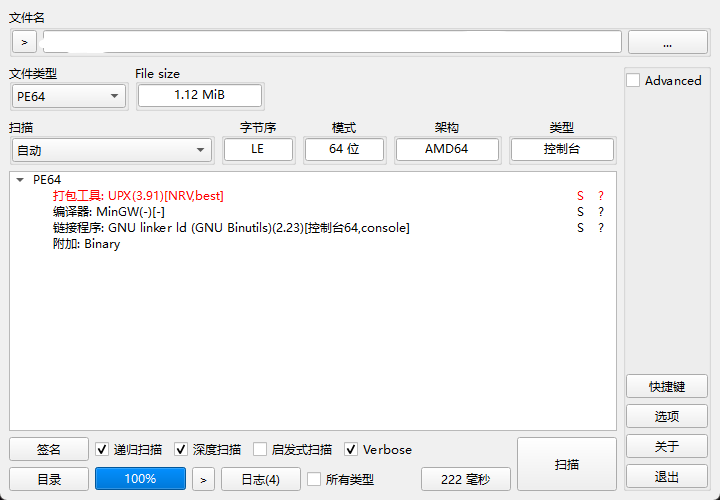
带有UPX壳,直接用工具脱会报错,打开010Editor,将小写的upx改为大写的upx即可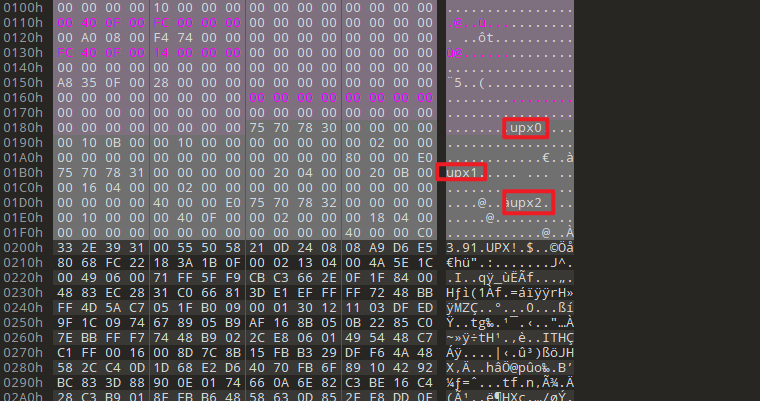
修改之后,就可以一键脱壳了
1 | |
手动脱壳
自己做的时候没有注意到大小写的问题,也就借此机会记录一下详细手脱的过程
使用的软件:x64dbg及其自带插件 Scylla
参考链接:https://www.anquanke.com/post/id/99750
首先使用ida找到大跳转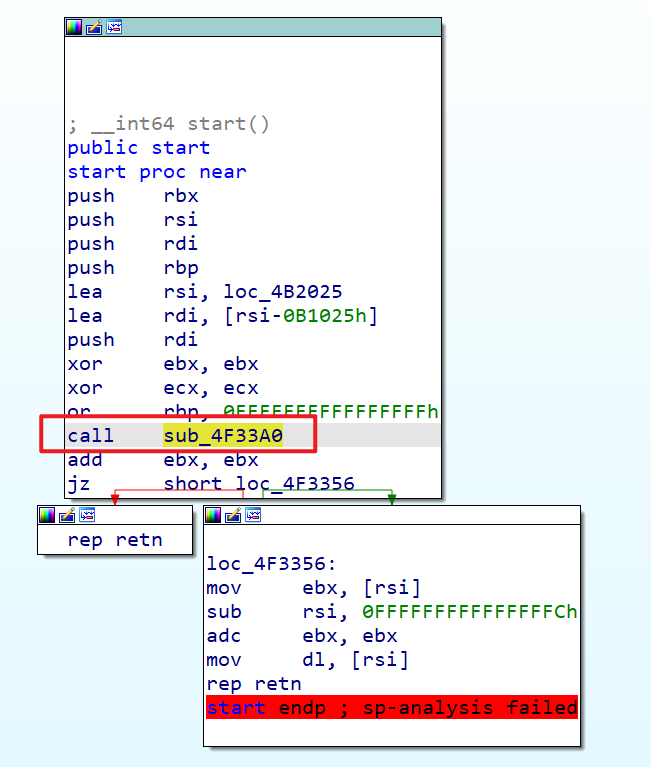
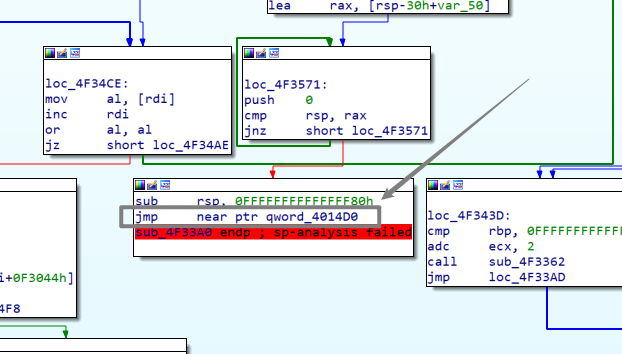
在x64dbg中找到这个jmp直接,跟进去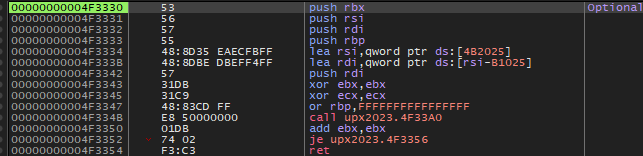
找到OEP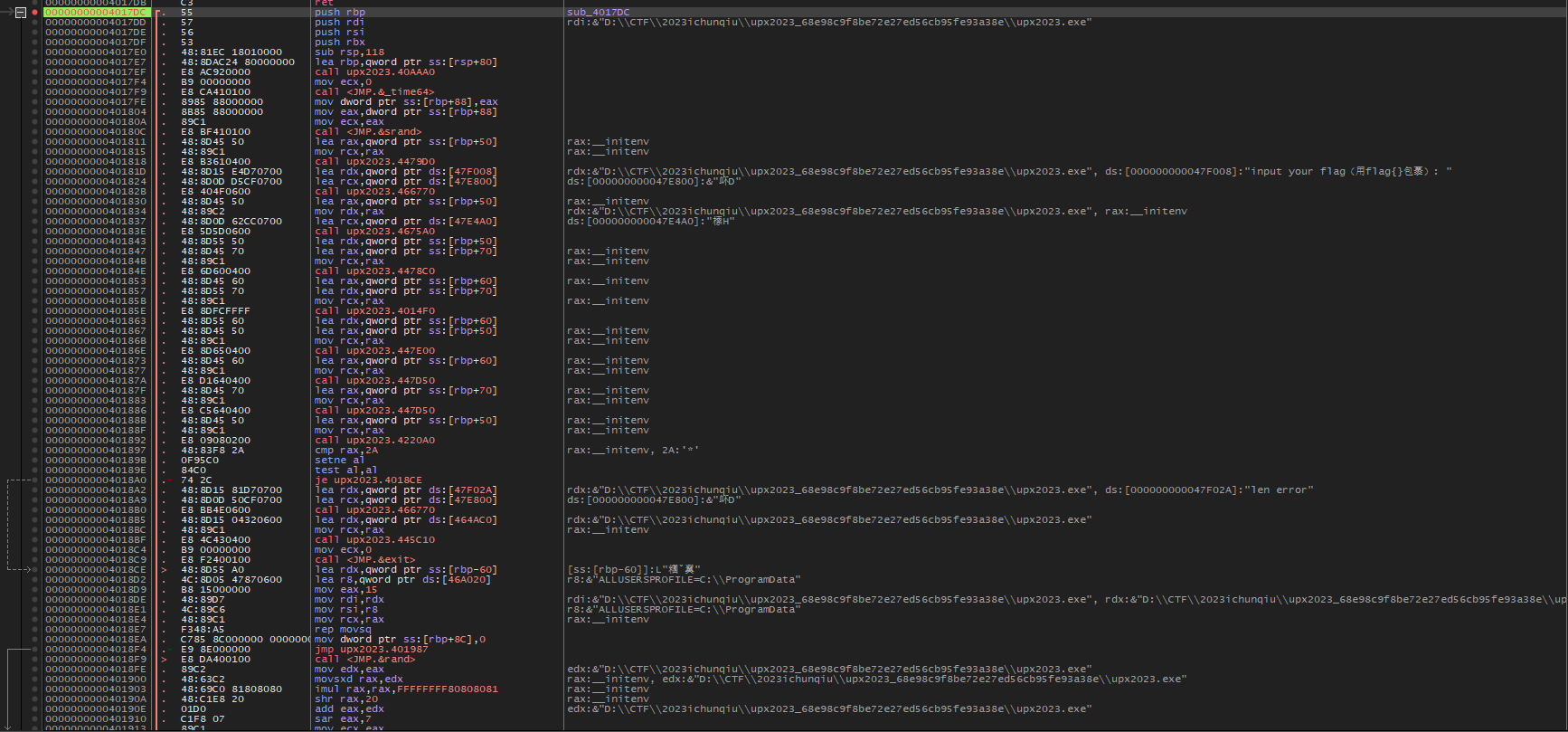
选择插件 Scylla dump另存为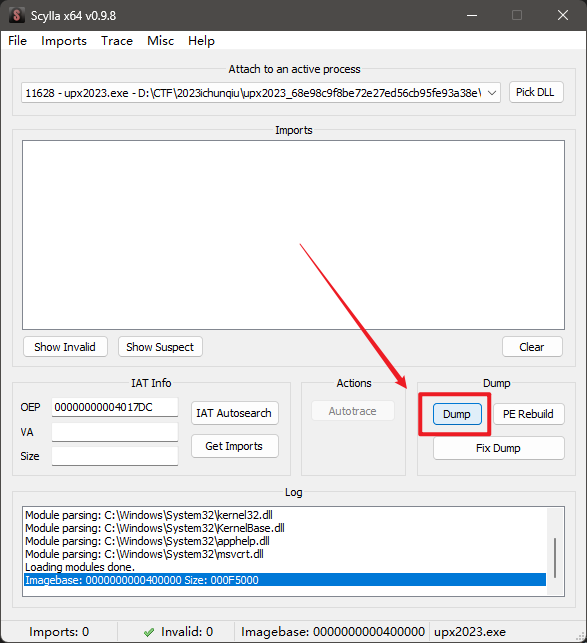
dump完成后修复IAT表,首先搜索IAT表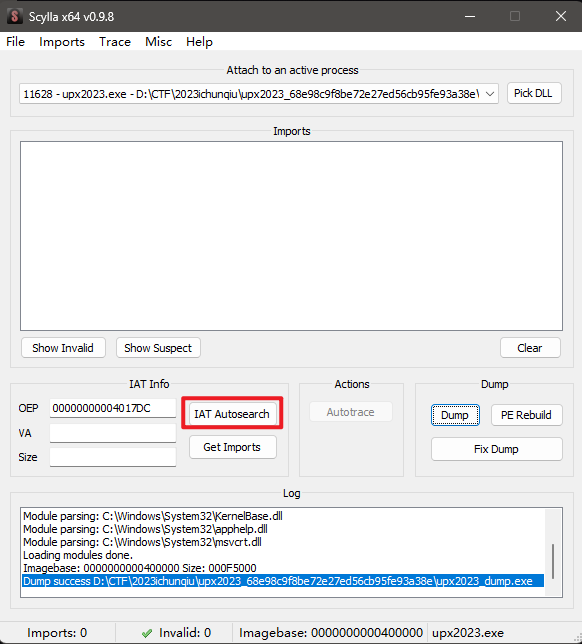 Get
Get
Imports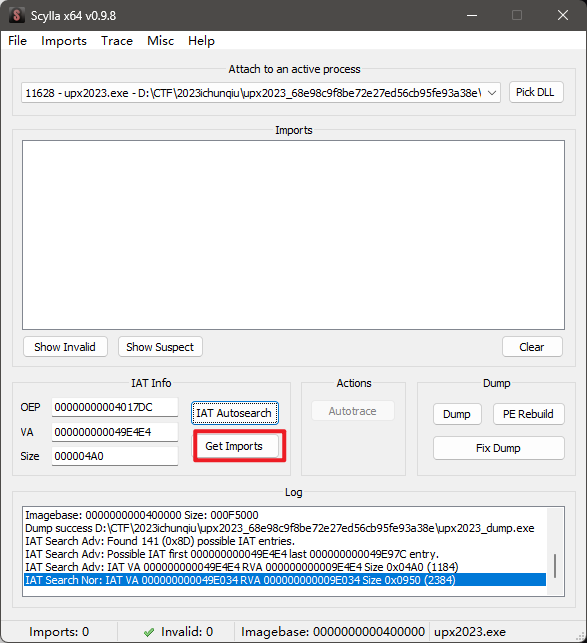
修复Dump出来的文件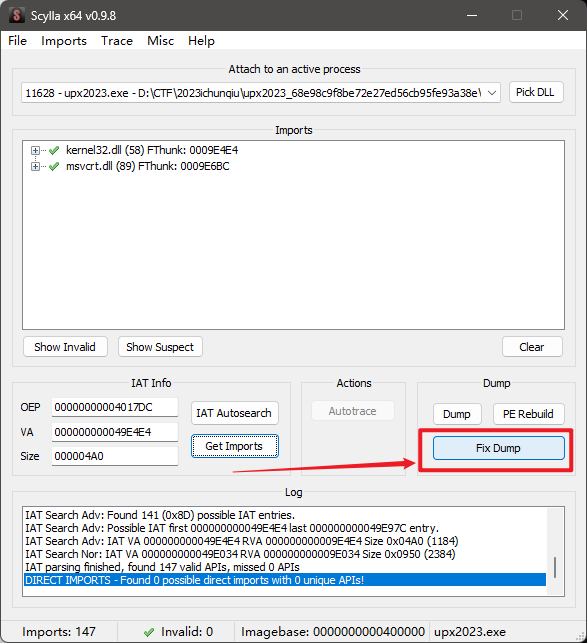
出现下面的情况表示修复成功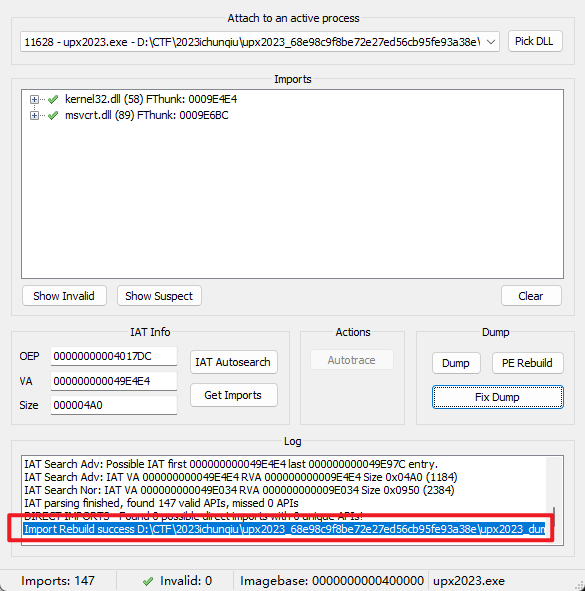
我们可以直接运行试试
1 | |
可以运行,脱壳成功
但是电脑重启之后好像就不行 了…
并且对照工具脱壳后的结果,差异有点大,主要是在符号上
0x1 分析
main函数的逻辑比较清晰
1 | |
大概流程:输入经过打乱顺序后->判断长度是否为42->以当前的时间为种子生成随机数,使用该随机数异或打乱后的flag-> 进行对比
打乱顺序可以通过调试得到固定的次序
1 | |
根据上述关系可进行还原
0x2 求解
分析的重点是对随机数的处理,首先我们通过提示知道flag的格式是flag{xxxxx},那么我们可以通过异或还原出六个随机数,并且通过打乱顺序后字符串确定其索引
1 | |
通过网站得到出题前的 2023.1.1的时间戳 Epoch Converter - Unix Timestamp
Converter和文件的修改时间的时间戳,写爆破
1 | |
得到异或值
1 | |
根据异或值得到flag
1 | |
file_encryptor
0x0 去花指令
TLS回调函数里面有反调试,TLS回调函数和main函数里面有异常处理,这些干扰了我们的分析
首先处理TLS回调函数中的反调试和异常处理
1 | |
过了反调试后,程序会在00401901触发异常,该异常的处理在00401916,那么从004018DA到00401916这一段的代码应该是可以直接patch掉的,Patch后:
1 | |
接下来处理main函数
1 | |
004019B4处的异常触发会跳转到004019CC,从004019A3到004019CC之间的代码都可以nop掉
这里有一个花指令
1 | |
1 | |
sub_842140 函数中调整了函数返回后的下一条地址,也就是返回地址是
008419FB,patch修改一下
1 | |
修改后就可以见到较为完整的伪代码了
1 | |
类似的花指令还有
1 | |
同样的进行Patch处理
1 | |
此时整个程序就较为清晰了
0x1 分析
相当于附件中还有另一个程序,程序先加载这个程序,然后进行解密,解密后得到
1 | |
在函数sub_F81050中,检查了卷序列号
1 | |
卷序列号是一个唯一标识磁盘卷的数值,这里我们需要手动跳过一下,或者修改程序,直接让其返回
1 | |
上述代码遍历了用户目录的文档目录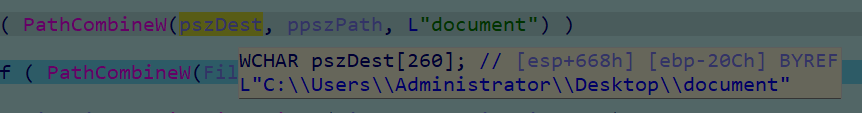
形成了通配符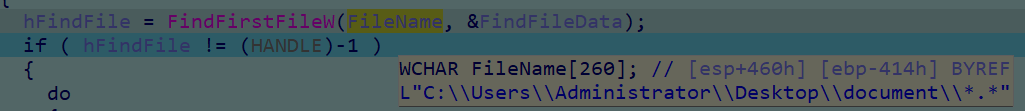
得把文件放到这个目录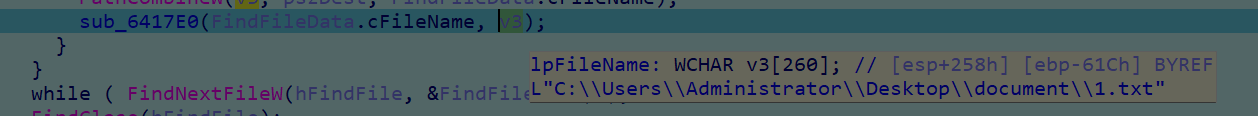
进入函数之后,发现有rsa相关特征
1 | |
跟进去之后,调用了解密的cryptsp.dll
因为是对文件进行加密,我们直接找到加密的地方
1 | |
这里的v6是dll中的一个函数,跟进v6,调用了 rasenh.dll 中的CPEncrypt函数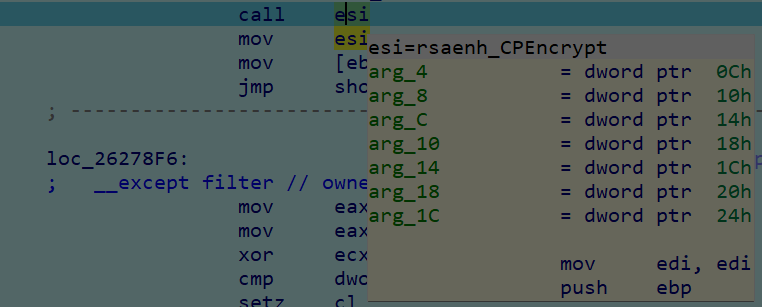
经过调试呢,发现就是这里进行的加密,也就是CPEncrypt函数进行加密
0x2 求解
去分析这个文件的加密有点复杂,因为这个dll里面是有解密函数的,我们可以通过更改调用函数实现解密
找到CPDecrypt函数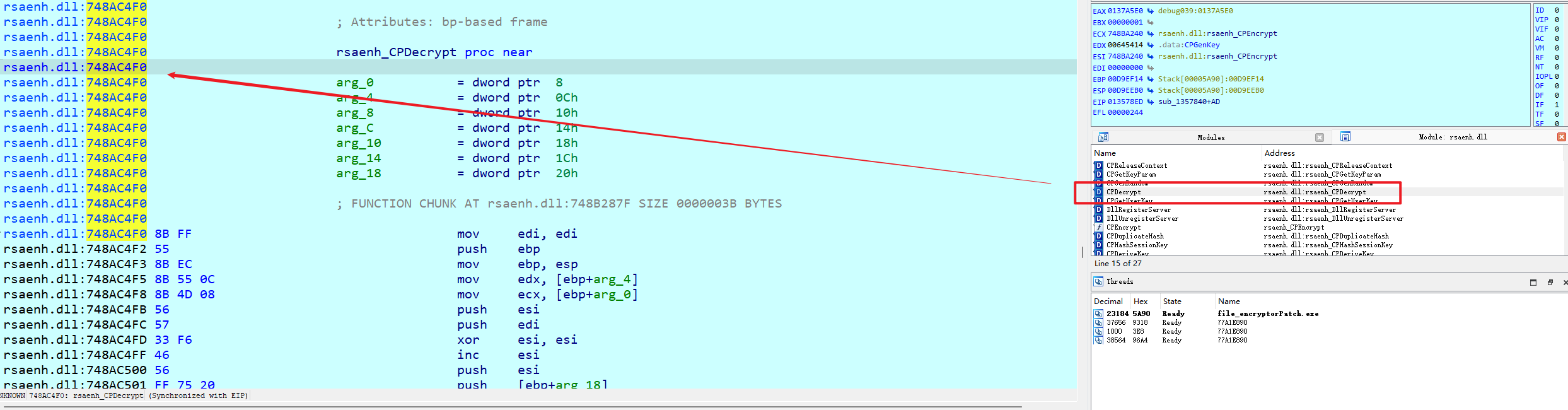
将esi寄存器的值修改为这个,直接F9 之后看1.txt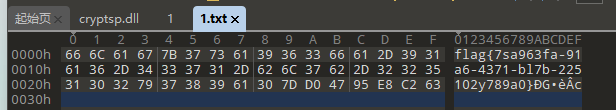
得到了flag
coos
0x0 分析
main函数
1 | |
可知长度是32,在主要的加密函数中有一个switch语句,还有很多分支,分析了一下,发现是一个虚拟机逆向,大概是个用32位模拟64位环境的过程
调试分析较为麻烦,这里就使用之前用过的idapython来使得在调试的过程中能够打印出相应的操作
0x1 IDApython 脚本编写
我将switch语句中用到的一些函数进行了分析,用一些指令来表示他们
这里面的PUSH 和 POP 写的有点随便
然后在适当的位置下断点,通过读取寄存器的值,打印当前函数的主要功能
1 | |
处理得很慢,大概需要个十分钟左右,得到下面的结果(因为是8字节一组的加密,这里只选取一组数据,并展示其的几十行)
1 | |
其中,有一些数据的来源无法确定,还需要经过调试。
0x2 复现算法&求解
经过调试后,发现其加密算法大概如下
1 | |
根据上述写出解密算法
1 | |
在处理对比数据的时候,还是需要调试情况下去获取,并不是在一个连续的内存空间上